Cryptography, you must have heard this term a lot since Bitcoin came into existence. But what exactly is cryptography? It is basically the study or practice of transferring encrypted data or messages between two or more entities.
This science of encrypting data changed the whole data transfer game.
The concept of encrypting data is not new. Even before the digital era, encryption was done using simple rules and physical tools to hide messages from enemies. Ancient Greeks used the scytale, and Romans used the Caesar cipher. These methods show that long before computers, people already used encryption to protect sensitive information.
Technology advancement has made data transfer easier, but it comes at a cost: the data is vulnerable to many threats, such as corruption and theft. The more sensitive the data, the higher the vulnerability is.
In a basic process of text encryption, a plaintext (data that can be clearly understood) undergoes an encryption process that turns it into ciphertext (which is unreadable).
By doing this, one can guarantee that the information sent can only be read by a person in possession of a specific decryption key. Cryptographic encryption is not only for payments across the internet. When two computers send data, every message, email, and everything is encrypted. Just the level of encryption depends on how sensitive the data is.
In the crypto realm, what role does cryptography play?
The term “crypto” in Greek means secret or hidden. The term cryptocurrency came up because of cryptography. Cryptography is what makes cryptocurrencies work. Blockchains like Bitcoin use it to secure transactions, prove ownership, and operate as a decentralized public ledger.
Cryptography is the invisible referee making sure nobody cheats in digital transactions. It ensures that value can be sent over the internet securely, without relying on banks or other arbiters. In simple terms, cryptography ensures that transactions are private, authentic, and unforgeable.
Public and private keys: the lock and key system
Public-private key systems are used in most cryptocurrencies. The public key is like your address; you can share it with others. The public key acts as your address, which can be shared, and the private key is like the key to your house, it’s the only thing that lets you access and use your funds.
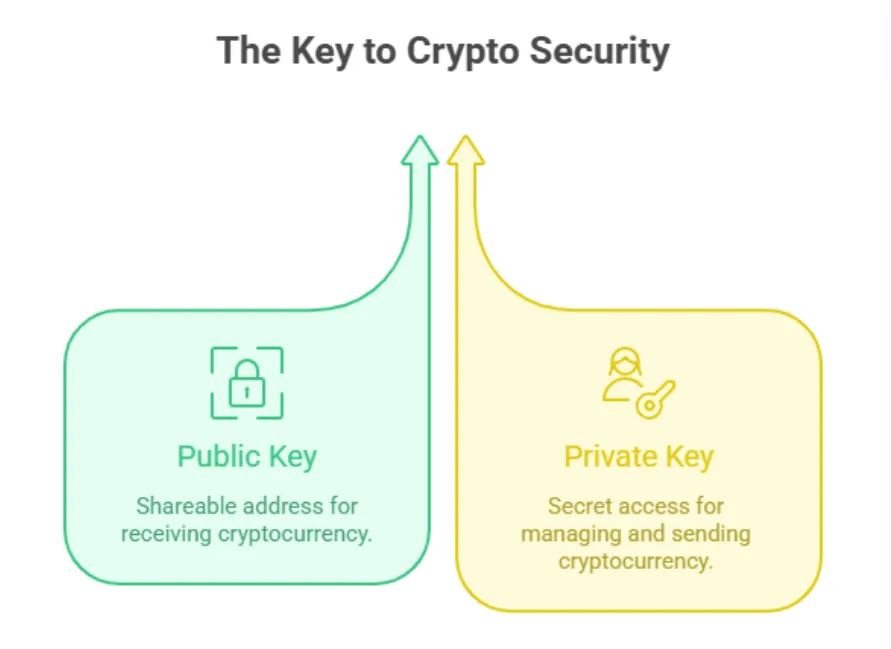
This guarantees that no one else can access or spend your cryptocurrency. Whoever controls the private keys controls the funds. Lose the key, and the money is gone forever; share it, and someone else can take everything. A crypto wallet is not where the coins are stored. Instead, it holds your private keys. The coins exist as records on the ledger. Whoever controls the private key controls the funds linked to it.
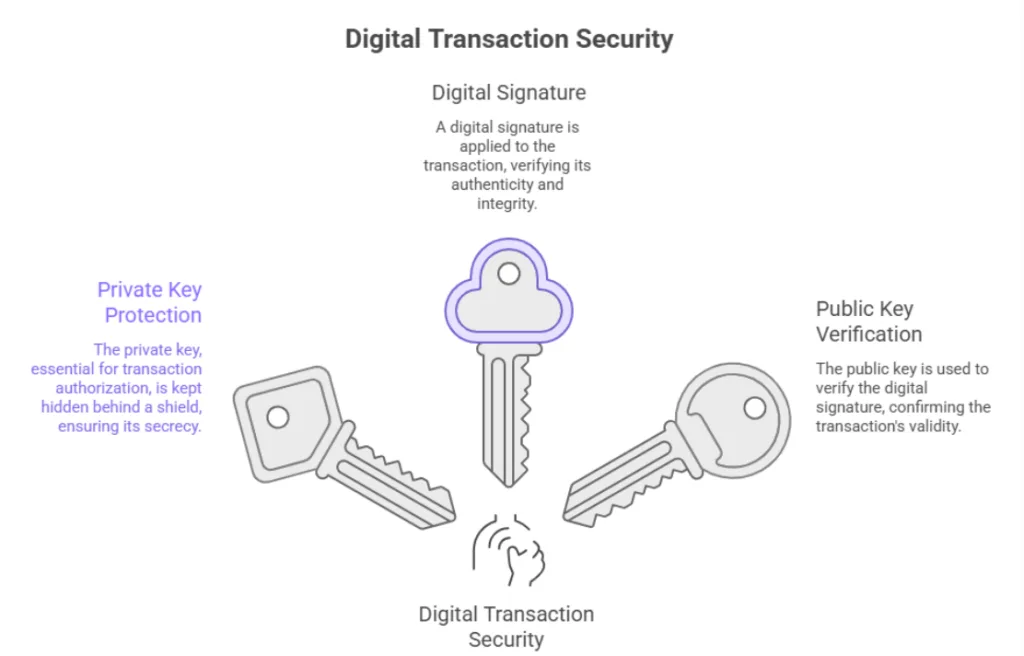
Digital signatures: proving it’s yours without giving anything away
When a transaction is done, it gets approved with a digital signature. This signature shows that you own the connected private key, without exposing the key itself. The signature is checked with the public key, which confirms the transaction is valid. keeping the private key safe.
Hash functions and one-way security
A hash function is like a digital fingerprint machine in that it takes any kind of data (a file, a transaction, anything) and gives you a string of letters and numbers that is always the same length, no matter how big the input is.
SHA-256 is the hash function that Bitcoin uses. It makes a 256-bit (64-character) hash. With 2²⁵⁶ possible outputs, collisions are basically impossible, more combinations than atoms in the universe.
This is why hashes secure everything: tamper with one transaction, the hash changes, the whole block (and chain) breaks, and everyone sees it instantly. No trust needed, just math.
Bitcoin uses SHA-256, which is a very secure cryptographic hash function. It keeps transactions safe, makes sure data stays untampered, and sits at the core of how mining actually works.
Double spending and how cryptography solves it
Double-spending happens when someone tries to spend the same digital coins twice. Cryptography stops this by tying each transaction to its sender, with a distinctive signature, and sharing it across the network. Once written on the blockchain, those coins are marked as spent, and any reuse is rejected. The first valid transaction goes through, the rest are ignored.
The first cryptocurrency appeared in 2009, not because someone invented brand-new cryptographic tools, but because the right combination finally came together, public-private keys, digital signatures, secure hashing, peer-to-peer networking, and time-stamped blocks. This integration turned long-existing cryptographic ideas into the foundation for truly decentralized digital money.