Imagine a scenario where someone could instantly crack your password, unlock your crypto wallet, and rewrite financial history on the blockchain. Right now, that sounds far-fetched. But advances in quantum computing are slowly moving us closer to a reality where the math protecting our digital money could be broken.
What blockchains really are
At its core a blockchain is a digital ledger, like a constantly developing notebook shared by thousands of people around the world. Instead of one person holding the notebook and making changes, everyone gets a copy and updates are only accepted if the majority agree they are valid. This creates trust without needing a bank or central authority.
Each page of the notebook is a block filled with transactions. Once a block is full it gets sealed and linked to the previous one, forming a chain. Because each block depends on the block before it, rewriting history becomes nearly impossible. That is why blockchains are often described as tamper resistant.
This makes blockchains useful for things like Bitcoin, Ethereum, and many other applications where people want a trustworthy record without relying on banks or governments.
Secret glue to the system: Cryptography
Blockchains rely heavily on cryptography, which is the science of keeping secrets safe using math. There are three pillars upholding the system:
Hash functions
A hash is a kind of digital fingerprint. When you feed any data into a hash function, it produces a string of numbers and letters of fixed length. The tiniest change in the input completely changes the output. That makes hashes perfect for securing blockchain blocks.
For transactions, blockchains rely on public key cryptography. There are two important systems to know here: RSA and elliptic curve cryptography (ECC).
RSA encryption
RSA works by using very large prime numbers. You have a public key that everyone can see and a private key that only you know. The public key is created in a way that makes it practically impossible to reverse engineer the private key with normal computers because factoring extremely large numbers would take ages.
Elliptic curve cryptography (ECC)
Elliptic curve cryptography uses math on elliptic curves. Instead of factoring primes, it relies on the difficulty of solving what’s called the discrete logarithm problem. In simpler terms, it is easy to multiply points on a curve but ridiculously hard to reverse the process. ECC gives the same level of security as RSA but with much smaller key sizes, which is why it has become the standard in blockchain.
On ordinary computers, breaking these systems would take far longer than the lifetime of the universe. That’s why they’ve been considered safe, until quantum computing entered the picture.
Classical vs quantum computers
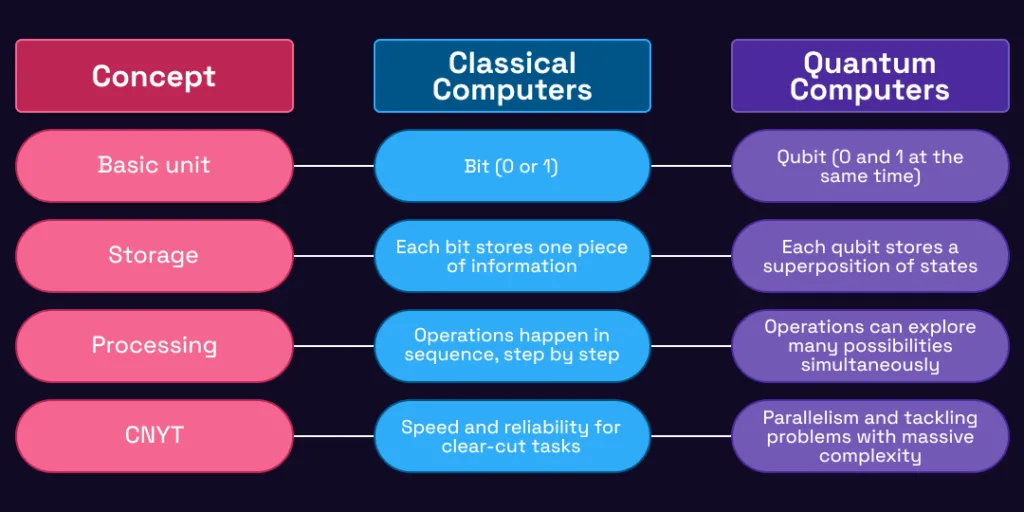
To appreciate the difference, let’s compare how normal computers and quantum computers operate.
In classical computing, everything boils down to zeros and ones, tiny switches that are either on or off. A qubit, the unit of quantum computing, can exist in a mix of both zero and one at once, thanks to superposition.
When you string qubits together, they can also become entangled, meaning the state of one qubit affects another no matter the distance. This opens the door for quantum machines to solve certain problems exponentially faster than classical ones.
The state of quantum computers
Despite the hype, quantum computers are still in their infancy. Companies like IBM, Google, and startups such as Rigetti and IonQ are building prototypes with tens or hundreds of qubits. But these machines are noisy, unstable, and prone to errors. Running a useful algorithm often requires thousands or even millions of stable “logical qubits,” which is far beyond what we have right now.
That said, research is advancing quickly. IBM has a roadmap for a million-qubit system within the next decade or two. Governments and corporations are pouring billions into the field, not just for cryptography but for chemistry, optimization, and artificial intelligence. While today’s quantum computers cannot break blockchain cryptography, tomorrow’s might.
The threat to cryptography
The fear comes from specific quantum algorithms that target the very foundations of cryptography.
- Shor’s Algorithm: This is the most famous. It can factor large numbers and solve the discrete logarithm problem efficiently. That means both RSA and elliptic curve cryptography could be broken if a sufficiently powerful quantum computer runs Shor’s algorithm.
- Grover’s Algorithm: This algorithm speeds up searching through possibilities. It effectively cuts the strength of hash functions in half. So while SHA-256 (used in Bitcoin) is currently very secure, Grover’s algorithm could make brute-force attacks twice as fast on a quantum computer. It wouldn’t destroy blockchain alone but weakens its defenses.
These are not just theoretical. They are working algorithms, proven in labs on small scales. The only barrier is building a large enough quantum machine to run them.
Building quantum-resistant blockchains
The good news is the crypto community is not sitting still. Researchers are designing quantum-resistant or “post-quantum” cryptographic systems. These often rely on mathematical problems that even quantum computers struggle with, such as lattice-based cryptography, multivariate equations, or hash-based signatures.
Some experimental blockchains like the Quantum Resistant Ledger already exist. Major networks like Bitcoin and Ethereum are beginning discussions on migration. NIST, the standards body in the United States, has already selected algorithms such as CRYSTALS-Dilithium and Falcon as recommended post-quantum schemes.
Ethereum becoming quantum-resistant
Ethereum relies heavily on elliptic curve signatures (specifically ECDSA and BLS signatures for validators). To become quantum-resistant, Ethereum would need to swap these out for post-quantum alternatives. That sounds simple, but it involves several massive challenges.
Every Ethereum wallet would need to support new signature schemes. Validators would need to upgrade their software and hardware to handle new cryptography, which may use larger keys and slower operations. The protocol itself would require changes to transaction formats. There is also the need for coordination among millions of users, developers, and validators to ensure the switch does not fracture the network.
Metaculus's median date for when quantum computers will break modern cryptography is 2040:https://t.co/Li8ni8A9Ox
— vitalik.eth (@VitalikButerin) August 27, 2025
Seemingly about a 20% chance it will be before end of 2030.
Ethereum co-founder Vitalik Buterin recently pointed to forecasting platform Metaculus, where the median prediction for when a quantum computer will first break modern cryptography is the year 2040. While quantum breakthroughs could still be decades away, the possibility of earlier advances makes it risky for blockchains to wait until the last minute to adopt quantum-resistant measures.
So is the future of blockchain security looking bleak?
Quantum computers are still years away from being a direct threat. But the process of securing blockchains against them will take years too, and that is why the conversation has already started.
Blockchain has always been about trust without relying on middlemen. To keep that promise in the quantum era, its foundations must evolve. Whether you are a developer, investor, or simply curious, the story unfolding here is one of technology pushing technology.